Get to Know the latest variants of ransomware

Ransomware can easily involve us with their crimes and damages: You are browsing the web or checking out an email that suddenly a message appears on your screen and warns that your device and its stored data is locked/encrypted by a ransomware. As a result, you will not be able to access your information until you pay the requested ransom.
Many users are familiar with the procedure with ransomware, and as a result, attackers behind these cyber threats continue their quest to find new and innovative ways to force users to pay. In this article, we introduce you to the seven different types of ransomware that you need to recognize.
Cerber
Computers are usually infected with Cerber ransomware via an email attachment posing itself as a Microsoft Office document. In this situation, your data is encrypted, and each file receives a new extension as .cerber. This ransomware doesn’t activate in Russia, Ukraine, or other former Soviet republics.
A message on the screen will notify you that your computer has been infected with Cerber. You can also find instructions in TXT and HTML formats in all your folders on how to pay the requested ransom. You will also find a VBS (Visual Basic script) file which, when opened, will dictate instructions to you. Maybe this is the first ransomware that talks to you and explains how to pay the ransom and decrypt your data.
PUBG ransomware
In April 2018, new ransomware surfaced that followed a different approach to take your information hostage. In other words, PUBG ransomware gives you an option instead of asking money for decrypting your locked files:
– Play PUBG (PlayerUnknown’s Battlegrounds for $ 29.98 on Steam)
– Or just paste the provided code on-screen and you’re good
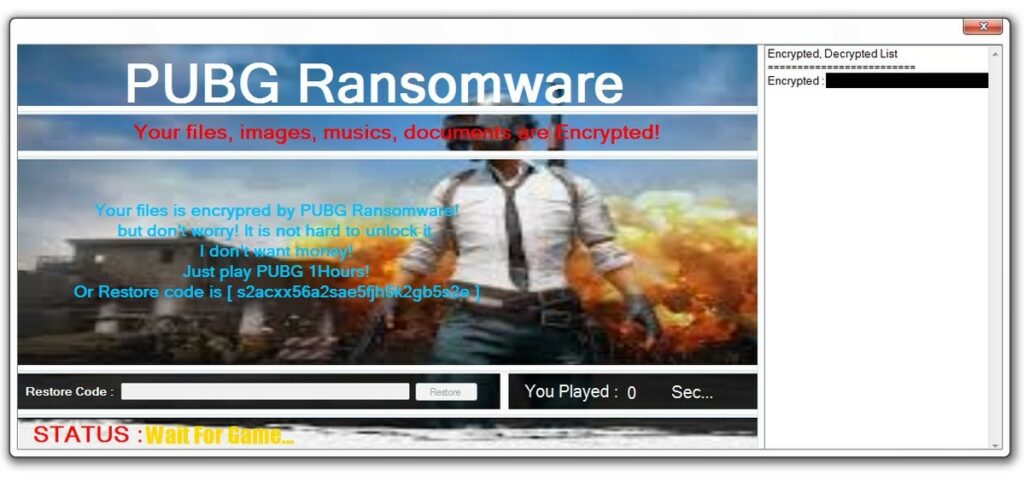
Thus, PUBG malware is not too bad, and although it is potentially annoying and pretending to be real ransomware, it doesn’t actually do anything more than promoting a game. Of course, let’s consider the fact that this ransomware really encrypts your files and change their extension to .pubg. However, if you find it difficult to get stuck between the option to copy the provided code in the field or to buy a three-star game, think that if you were involved with a real ransom, you had to pay a lot more money. So, maybe you should take security measures more seriously.
Unfortunately, PUBG ransomware is one of the few ransomware that you can easily get rid of, and this is not true of the vast majority of other ransomware.
Jigsaw
This ransomware is one of those criminals who doesn’t value their hostages’ life. Simply put, Jigsaw will delete your files one by one until you pay the ransom. Although locking your data in an uncertain state is unpleasant enough, the malware takes the scam further. The Jigsaw ransomware, originally known as BitcoinBlackmailer, gained its new name from Billy the Puppet’s presence in the Saw movie series.
The Jigsaw ransomware, first seen in April 2016, spread via spam emails and infected attachments. After the activation, the ransomware locks the victim’s system data and its MBR (Main Boot Record) and then displays a message. This message is basically a threat. If a requested ransom (by Bitcoin) is not paid within one hour, a file will be deleted from your computer. Every hour delay in payment will just increase the number of deleted files. Meanwhile, trying to reboot the system or terminating the process (Jigsaw poses as the Firefox browser or Dropbox interface in the Task Manager) will merely result in 1000 files being deleted.
If the Jigsaw isn’t still dreadful enough for you, latter versions of it threaten the victim that will publicly publish their information if they do not pay the ransom. In this way, Jigsaw incentivizes the victim through menaces, rushing the games of malware and ransomware to a new level.
Ranscam
Apparently, we are all familiar with the story of involving with ransomware: your device is infected with malware that encrypts your data and then forces you to pay money to free them up. After paying the ransom, you will get the key to decrypt your data. Well, although the situation is often in this form, the procedure does not apply to Ranscam.
Just when you think everything is solved, this ransom uses the method of taking the money and run without bothering to decrypt your data and thus your data is lost. Although it’s clear that most ransomware scams are written by professionals, there is some doubt over the proficiency of the hand behind Ranscam. Even though this malware is not as advanced as other types of ransomware, it is undoubtedly effective. The more notorious Petya ransomware was also known for the obliterating of information instead of returning the access to the victim.
TV malware
In June 2016, the FLocker that had previously hit Android phones and tablets, showed that it has evolved. In fact, it also added Android-powered Smart TVs to its list of targets.
FLocker is one of the ransomware types that displays a “law enforcement” warning. In other words, the ransomware informs you that illegal material has been viewed on your system!!!. The FLocker ransomware has been seen in many countries, almost anyone who isn’t in Russia, Ukraine, or any of the other former USSR nations. Like most ransomware, payment is demanded via iTunes vouchers, and after you pay the ransom, control of your Android device will be returned to you.
Fake ransomware
It may seem strange, but some types of ransomware actually don’t do anything. In fact, you should not confuse these types of ransomware with PUBG, because they simply display false warnings and claim to have control of your device.
Undoubtedly, coping with these types of ransomware is easy, but the power of the ransomware concept is enough to keep them lucrative for their writers in many cases. In other words, the victim will pay the requested ransom without knowing that there is no need to do so and his information is not encrypted at all.
These types of ransomware usually appear as a browser’s popup window that you can’t close, and it looks like there is no option other than paying attention to the warning inside the window and pay the ransom. If you want to check if you involved with a real ransomware or just a hollow threat, try closing the window. To do this, you can use Alt + F4 in Windows or Ctrl + W on the Mac. If the window closes, update your anti-virus software immediately and scan your system.
Ransomware in disguise
Eventually, it turns into ransomware that deceives its victim through their seemingly legitimate appearance. You probably know that fake email attachments are used to infect devices with ransomware. In this case, attachments appear as legitimate DOC files that are sent through spam emails claiming you owe money and the attachment is the invoice. After downloading this file (due to curiosity about debt reason), your device is compromised.
Of course, there are Other disguises to do this. For example, DetoxCrypto ransomware claims to be popular Malwarebytes Anti-Malware software, with a little change in its name (Malwarebyte). There is also a variant of Cryptolocker that pretends to be a Windows update.
Knowing various types of methods used by malware will help you stay alert in different situations and show a more accurate response to the situation. In today’s digital world, the first step in protecting yourself from cyber attacks is to make everything done consciously and carefully.
Related News










